Windows Server 2008 has a new security feature to allow configuration of fine-grained password policies to assign different password and account lockout policies to users and groups within a domain. The security options are designed for both user and computer configuration.
Before Windows Server 2008, if two admins had different password policies, they would have to split the users between two domains. Windows Server 2008 Group Policy gets rid of this administrative headache. For example, you can apply stricter policies to users that have access to classified information.
Fine-Grained Password Policy:
Before Windows Server 2008, if two admins had different password policies, they would have to split the users between two domains. Windows Server 2008 Group Policy gets rid of this administrative headache. For example, you can apply stricter policies to users that have access to classified information.
Password policy is configured by using a Group Policy Object (GPO) scoped to the domain. Each new domain created contains a Default Domain Policy GPO that is linked to the domain. Best practice is to edit the Default Domain Policy GPO to specify password policy settings for your organization. Do not define the password, lockout, or Kerberos policy settings for any other GPO. Do not use the Default Domain Policy GPO to define any other type of GPO. Password settings in the Default Domain GPO affect all user accounts in the domain.
Password settings can be overridden on the individual user accounts on the Account tab of a user's Properties dialog box. However, applying fine-grained policies to a group is more manageable than applying policies to individual user accounts.Configure a Domain Account Policy:
The Account Policies node contains settings related to user accounts, such as password policy, account lockout policy, and Kerberos policy. Kerberos v.5 is the default authentication protocol on all Windows domains running Windows Server 2003 SP1 and later. Use domain-based Group Policy to configure password policy settings to protect users of Windows 2000, XP, Vista, 7 client computers. Windows Server 2008 R2 provides default values for the available password policies.
- Click Group Policy Management and right-click to run with administrative credentials.
- Next, double-click on your domain name and click on Default Domain Policy and click Edit. This takes you to the GPME, Group Policy Management Editor. Expand Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies and select Password Policy. Below are the available policy settings.
- Double-click a policy setting to configure. Each policy setting has a tab that explains the purpose of the policy setting.
- Enforce password history policy is used to set the number of previous passwords to be checked. The default is 24. Active directory can check the cache of the user's previous hash codes to ensure the password has not previously been used.
- Maximum password age default policy setting is 42 days for the number of days a user has until required to change their password.
- Minimum password age default policy setting is 1 day for the minimum amount of time that must pass before resetting a password.
- Minimum password length default policy setting is 7 characters for the number of characters the password entered will be compared to.
- Password must meet complexity requirements policy setting is normally set to enabled to meet certain complexity default requirements which include the use of three or four character types like upper case, lower case, numeric, and non-alphanumeric.
- Store passwords using reversible encryption can be enabled for those applications that cannot use normal encryption. Using this policy is not recommended as it reduces the security of your domain as the password is in plain-text form.
Password policies are unique in that they apply only when configured in a domain-based GPO. Any configuration in GPOs linked to other containers is ignored.
When you enter a user name and password in an Active Directory domain, the credentials are authenticated against your Active Directory account. When a password is entered, and if it meets the password requirements, Active Directory puts the password through a mathematical algorithm that produces a unique hash code. The algorithm is called a one-way function, meaning the hash code cannot be put through a reverse function to determine the actual password. The actual password is not stored in Active Directory, only the hash code is stored in Active Directory.Hackers often use programs with dictionaries to run through plain text passwords until one works. This is called a brute-force attack. RainbowCrack is another type of password cracking that uses large pre-computed tables called rainbow tables. Rainbow tables can be very large so cracking a long password is not very feasible. That is why it is better to have long complex passwords, or use pass phrases as your password.
The Account Lockout Policy underneath Password Policy, limits the number of times a password can be entered. Windows 2008 sets default values for the account lockout settings. The Account lockout threshold is the number of invalid logon attempts permitted within a specified time set by the Account lockout duration policy. An Administrator can unlock the account or you can set the Reset account lockout after policy to automatically unlock the account after a specified period of time.
Fine-Grained Password Policy:
Fine-Grained Password Policy (FGPP) is built into Windows Server 2008. Fine-grained password policies are not implemented as part of Group Policy. There is a separate class of object used to maintain the fine-grained password settings. It is called the PSO, Password Settings object. PSOs are managed by a low-level tool called ADSIEdit, Active Directory Service Interface Editor. The Password Settings Container stores the PSOs and is created by default under the domain's System container.
More than one PSO can be created in a domain. The PSO contains attributes for the password and lockout policy settings. It has something called a multivalued link attribute that links the PSO to users or groups and has an integer precedence value that determines which PSO is applied in case of multiple PSOs being applied to that same user or group. The PSO with the lower integer precedence has the higher priority. Note: you cannot apply a PSO to an OU. If you want to apply the same password settings to all users in an OU, you should create a global security group and apply the PSO to that group. A user PSO takes precedence over a group PSO.
Creating a PSO:
To use a fine-grained password policy, your domain must be at a Windows Server 2008 domain functional level. You must be a member of the Domain Admins group, and you can delegate control of the task to other users.To check and/or raise the domain functional level, go to Active Directory Users and Computers, right-click the domain name, and select "Raise domain functional level". This allows you to see the current domain functional level before changing it.
Creating a PSO:
- Go to START\Run and type adsiedit.msc (part of Windows Server 2008).
- Right click ADSI Edit and click Connect To.
- If Default Naming Context and your domain name are visible, accept these. Otherwise, type the fully qualified domain name (FQDN) of your domain. Click OK.
- Expand your domain name and locate the CN=System container. Expand the System container and find CN=Password Settings Container.
- Right-click CN=PasswordSettings Container, click New, and click Object. You will see msDS-PasswordSettings. This is the object class referred to as PSO. Select it and click Next.
- You are prompted for the value of each PSO attribute. Click Next each time after you enter the appropriate values for the attributes.
- cn= This is the common name of the PSO. (You can name the PSO here)
- msDs-PasswordSettingsPrecedence: 1. A 1 means this PSO has the highest possible precedence.
- msDS-PasswordReversibleEncryptionEnabled: False. The password is not stored using reversible encryption.
- msDS-PasswordHistoryLength: 30. The user cannot reuse any of the last 30 passwords.
- msDS-PasswordComplexityEnabled: True. Password complexity rules are enforced.
- msDS-MinimumPasswordLength: 15. Passwords must be at least 15 characters long.
- msDSMinimumPasswordAge: 1:00:00:00. A user cannot change their password within one day of a previous change. The format is d:hh:mm:ss (days, hours, minutes, seconds)
- msDS-MaximumPasswordAge: 45:00:00:00. Password must be changed every 45 days.
- msDS-LockoutThreshold: 5. Five invalid logons within the time frame specified by the next attribute will result in account lockout.
- msDS-LockoutObservationWindow: 0:01:00:00. Five invalid logons, specified by the previous attribute, within one hour will result in account lockout.
- msDS-LockoutDuration: 1:00:00:00. When an account is locked out, it will remain locked for one day, until it is manually unlocked. A value of 0 means the account will remain locked until an Administrator unlocks the account.
- If you want to define more attributes, click More Attributes button. Otherwise click Finish and close ADSI Edit.
- Run Active Directory Users and Computers and expand the System container. If you don't see the System container, turn on Advanced Features by clicking on the View menu.
- Click the Password Settings Container.
- Right click the PSO (your PSO name), click Properties, and click the Attribute Editor tab. This tab displays all of the configured attributes for the PSO.
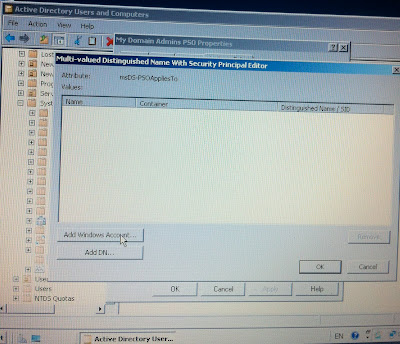
- In the Attributes list, select msDS-PSOAppliesTo, and click Edit.
- The Multi-valued Distinguished Name With Security Principal Editor dialog box appears. Click Add Windows Account. The Select Users, Computers, or Groups dialog box appears.
- Type the user or group name and click OK. The name you added is displayed when you return.
- The security identifier (SID) of the user or group appears in the Value column of the Attribute Editor tab. You can repeat this process as many times as you want to link the PSO to additional users or groups.
- Click OK to close the PSO Properties dialog box.
PSOs for the user take precedence over PSOs for the group for which a user belongs. PSOs for groups are applied according to the precedence value.
- Make sure Advanced Features is on in the View menu of Active Directory Users and Computers.
- Select the Users container or OU in which the user is located.
- Right-click the user account and choose Properties. Select the Attribute Editor tab.
- Click the Filter button. In the list that appears, ensure Show attributes:Optional, Show read-only attributes: Constructed, and Show read-only attributes: System-only are checked.
- Scroll the attribute list to locate msDS-ResultantPSO. The value displays the DN of the effective PSO. If the value does not display
, this means the password settings for the Default Domain Policy GPO are in effect for this account.
Fine-Grained Password Policies
Fine Grained Password and Account Lockout Policy Step-by-Step
Account Policies
http://www.gpanswers.com
http://en.wikipedia.org/wiki/Brute-force_attack
http://en.wikipedia.org/wiki/RainbowCrack
http://www.freerainbowtables.com/
Fine Grained Password and Account Lockout Policy Step-by-Step
Account Policies
http://www.gpanswers.com
http://en.wikipedia.org/wiki/Brute-force_attack
http://en.wikipedia.org/wiki/RainbowCrack
http://www.freerainbowtables.com/











No comments:
Post a Comment
"Comment As:" anonymous if you would rather not sign into an account!